Black mambas are fast, nervous, lethally venomous, and when threatened, highly aggressive. They have been blamed for numerous human deaths, and African myths exaggerate their capabilities to... Read more
To avoid fraud & spam registrations, phone verification is best way. So here we are going to create an demo application for phone verification system. To create this application we will... Read more
You’ve always heard that water is very good for health. But do you ever think that drinking water may harm you? Yes, According to Ayurveda, drinking water wrongly can cause more than... Read more
When we talk about gadgets, we talking on mobile phones, computer, laptop, tablets, ipod, games, smart watch and lot more gadgets available now days. No doubt, these gadgets very useful and... Read more
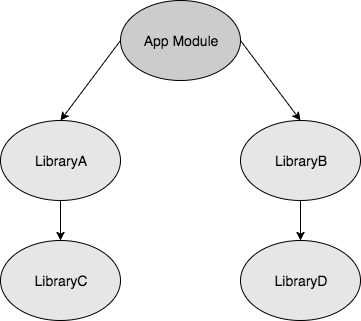
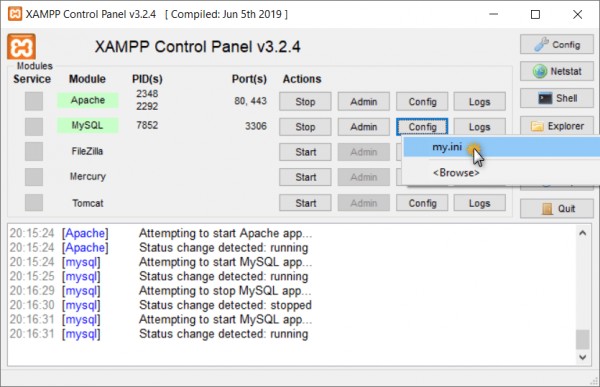
After update of Android Gradle plugin and Android Studio, if you getting error or warning something like this : Configuration ‘compile’ is obsolete and has been replaced with... Read more
The majority of website security breaches are not to steal your data or mess with your website layout, but instead attempts to use your server as an email relay for spam, or to set up a temp... Read more
What is SQL Injection ? SQL injection is an attack/attempt of hacking. A SQL injection attack consists of insertion or “injection” of a SQL query via the input data from the clie... Read more
SQL Injection is best prevented through the use of parameterized queries. The following chart demonstrates, with real-world code samples, how to build parameterized queries in most of the co... Read more